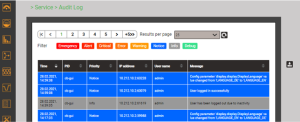
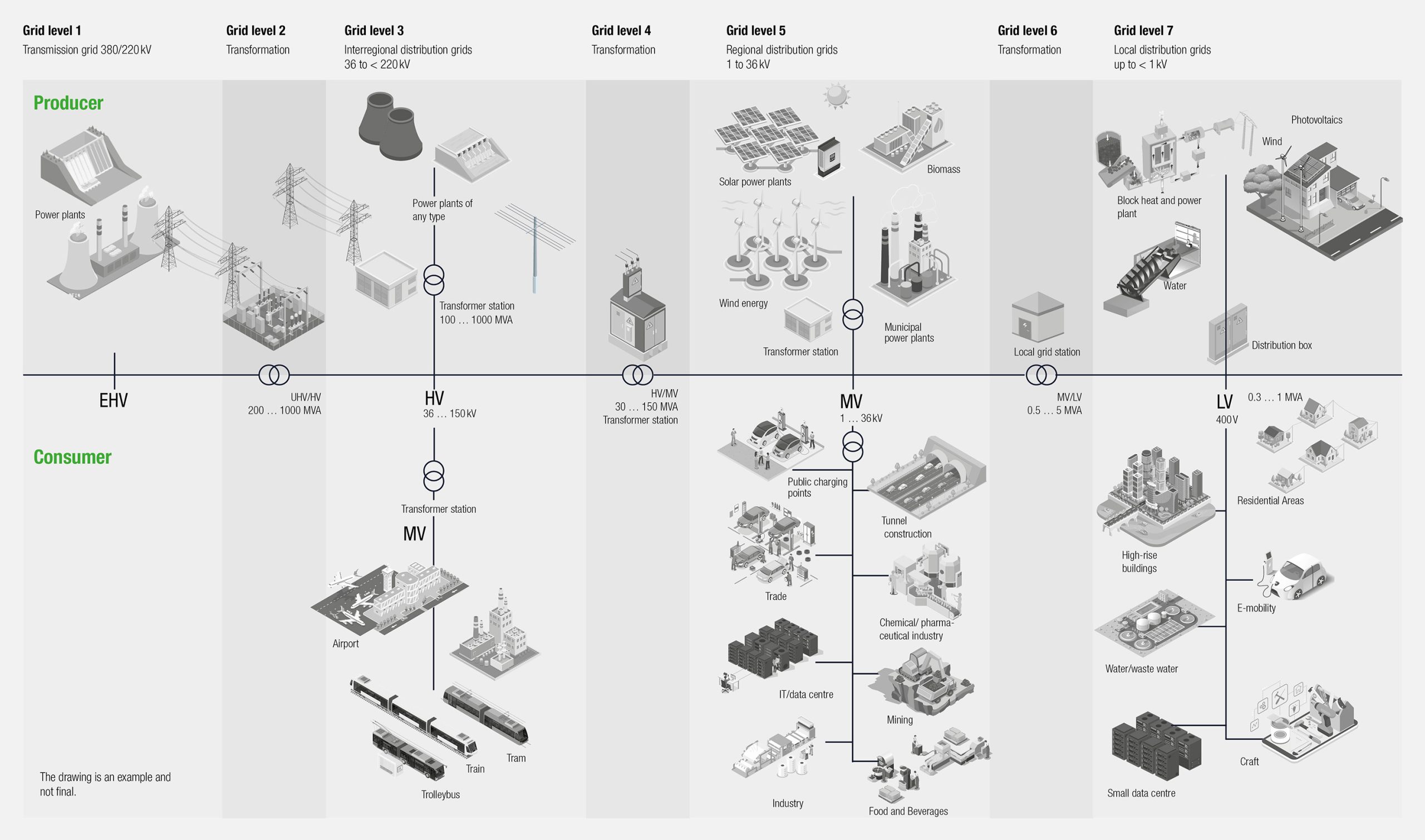
In the context of digitalization, the demand for cyber security is also growing enormously. “For example, 11% of German companies recorded an IT security incident in the past 12 months. Three out of ten companies expect to be targeted by cyber criminals in the next 12 months – organized gangs are particularly feared. The Ukraine war is fueling fears of more cyberattacks in this regard. [1]” The area of critical infrastructure, that which virtually keeps us alive on a daily basis, requires extra attention. For example, the electrical infrastructure, which will be highlighted in this article. The Swiss daily newspaper Tagesanzeiger (TA), for example, postulates in a “Survey on cyber security: Swiss electricity suppliers are insufficiently protected against hackers. The companies are particularly poor at recognizing attacks as well as responding to them. [2]”
This white paper addresses the fundamental dangers, the status quo, the laws in force in the EU as well as the currently practicable and available solutions in the context of electrical measuring instruments.
Due to the dynamic and challenging complexity of the topic, this report is intended as a guide and is not intended to be exhaustive.

![ClientWhitelist Informationstechnik; 09.08.2021]
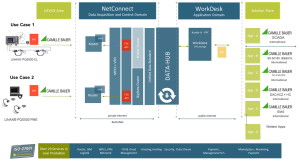
Möglichkeiten zur Daten-und Manipulationssicherheit
Quelle: Camille Bauer Metrawatt AG
Kontakt
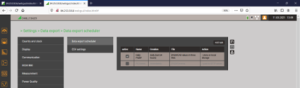
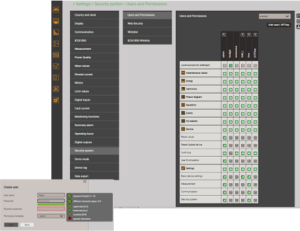
Rollenbasierte Zugriffsberechtigung (RBAC)
Gewähren von Nutzer-Rechten, die notwendig sind und nicht darüber hinaus
Zugriff auf Messdaten: Visualisierung, Löschen, Herunterladen
Konfigurationsdaten: Anzeigen, Ändern
Benutzerverwaltung
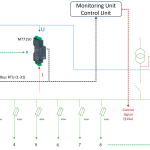
Fernzugriff über Website / Software
Lokaler Zugang
Keine klare Textübertragung von Login-Informationen
Wiederholte Anmeldeversuche erhöhen die Latenz
Speicherung der RBAC-Einstellungen nur verschlüsselt
RBAC
Hypertext Transfer Protocol Secure (https)
Sicheres Hypertext-Übertragungsprotokoll (abhörsicher durch Transportverschlüsselung)
Bidirektionale Verschlüsselung zwischen Server und Client
Stammzertifikate als Verschlüsselungselement
Geschützte Authentifizierung
Verschlüsselung des Dateninhalts
Verschlüsselung mit Camillebauer Zertifikat oder benutzerdefiniertem Zertifikat
RBAC
Client Whitelist / Client IEC61850 Whitelist [Firewall]](https://camillebauer.com/wp-content/uploads/2023/07/ClientWhitelist-300x67.png)